
Program comparison is an important function in information security, mainly used to prevent and identify unauthorized file changes,
protecting and preventing code or configuration files from being unintentionally modified or maliciously tampered with,
or becoming a channel for hackers' malicious viruses, causing the program to fail to execute correctly.
After setting up the program comparison function, the system will regularly perform a complete binary comparison of these files,
checking if every bit is completely consistent with the original file.
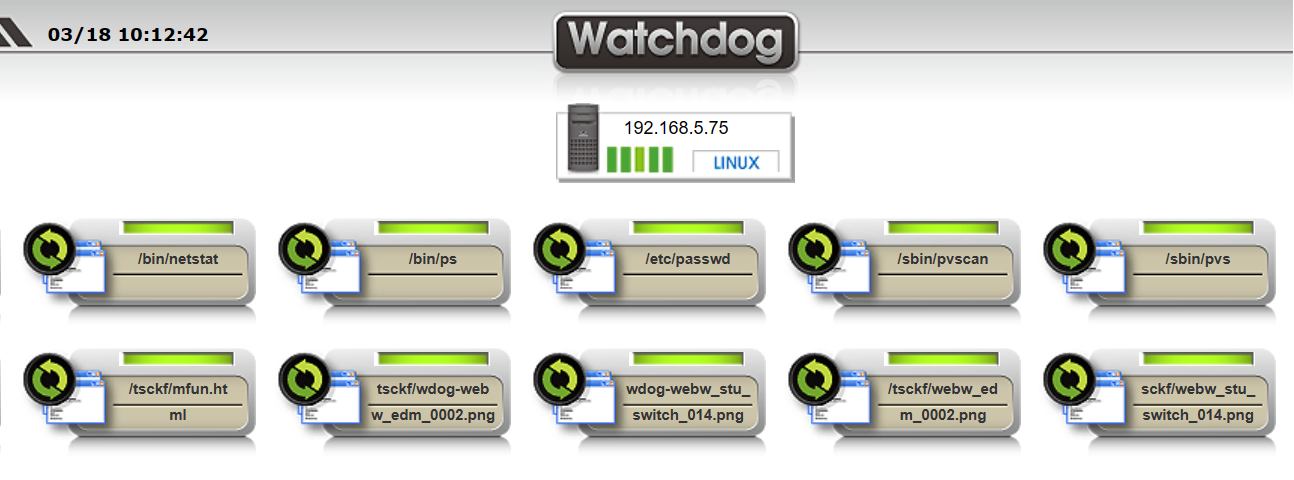
Program comparison mainly involves archiving high-risk files first, then performing 100% binary comparison regularly. File types include:
➢ Binary program files (.exe, .dll)
➢ Shell Script program files
➢ System configuration files
➢ Text files
➢ Password files
➢ Binary image files
System Specifications for Monitoring Program Comparison
➢ Detection Purpose: 100% binary comparison to check if the specified program or file matches the archived original file
➢ Monitoring Target: Program or file name
➢ Alert Conditions: Differences in comparison
➢ Real-time Information: Normal/Alert publication
➢ Information Collection: Messages, alert publication/release times
➢ Emergency Response: Notification, execution of predefined programs
➢ Alert Threshold: Differences in comparison