Watchdog's 【Scheduled Tasks】 function essentially serves as a process management and monitoring mechanism.
It automatically executes a series of programs or scripts based on a predetermined schedule,
thereby achieving continuous monitoring of system status or periodic collection of event logs.
The 【Scheduled Tasks】 can be viewed as an itinerary or workflow,
which includes a series of predefined tasks (such as "Task 1", "Task 2", "Task 3").
Each "Task" corresponds to a program provided by Watchdog, which may collect event logs, disk information, etc.
After each "Task" is completed, the system can choose to further process or filter the results using other programs provided by Watchdog.
Overview of the 【Scheduled Tasks】 Function
Through the following steps, the 【Scheduled Tasks】 function allows advanced users to customize IT operations monitoring details:
➢ Users can define their own executable programs or shell scripts to flexibly meet diverse IT operations needs.
➢ Set scheduled tasks to activate specific programs, ensuring important tasks are executed on time.
➢ Automatically collect and analyze the results of specified programs, providing real-time system status.
➢ Use logical operators such as and, not, or to precisely match alert strings and respond promptly to potential risks.
➢ Customize follow-up processes based on program results, enhancing efficiency.
➢ Integrate with the WATCHDOG system to achieve standardized control and ensure system security.
System Specifications for Scheduled Tasks
The monitoring system specifications of 【Scheduled Tasks】 are meticulously designed to focus on the following key points:
➢ Detection Purpose: Automatically execute programs at scheduled times, collect and analyze results, and carry out subsequent processing based on the results.
- Keep records, compare alarm conditions, and hand over to subsequent programs for processing.
➢ Monitoring Targets and Alarm Conditions: Focus on the textual content of the program to achieve precise monitoring.
➢ Real-Time Information and Information Collection: Provide real-time updates of normal and alarm states, collect key messages and alarm timestamps.
➢ Emergency Handling and Alarm Thresholds: Define specific response measures and alarm thresholds to ensure quick and effective problem resolution.
Practical Example
In addition to using 【System Logs - SYSLOG】,
you can also use 【Scheduled Tasks】 to customize Event ID reports based on user needs.
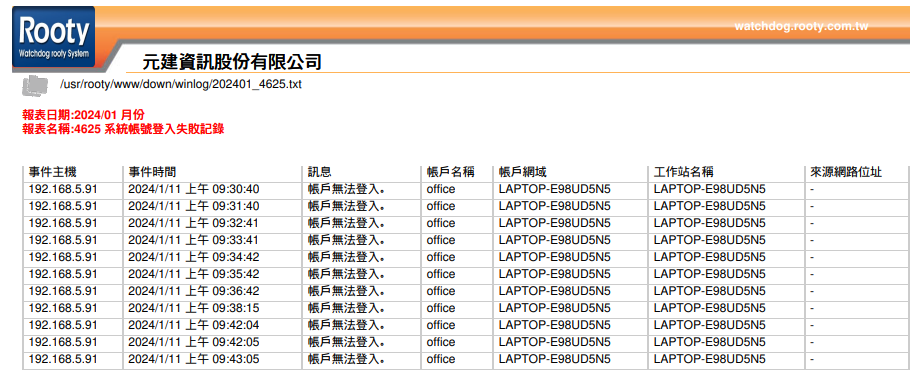
For example, if a client only needs to monitor and collect specific Event IDs, such as "4625 Account Logon Failure" and "4723 Attempt to Change Account Password" on a host,
the 【Scheduled Tasks】 function can be used to precisely create related reports. Specifically, the following two types of reports can be generated:
➢ Consolidate and report event logs for Event IDs 4625 and 4723 by server host IP.
➢ Summarize logs for Event IDs 4625 and 4723 across various server hosts.