
Assist in detecting network environment security through IP and MAC control
【IP and MAC Control】is one of the auxiliary monitoring functions of the network environment security application system layer.
It can bind the device's IP and MAC, and compare them regularly. Once an IP/MAC mismatch is detected, an alert will be issued.
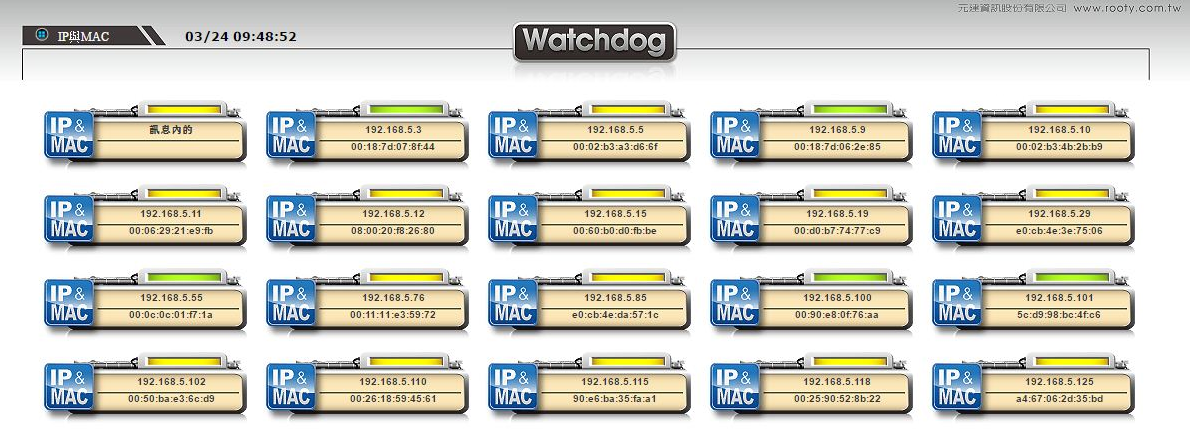
System Specifications for Monitoring IP and MAC Control
➢Detection Purpose: Reduce the risk of IP conflicts and prevent illegal device connections.
➢Monitoring Targets:
- MAC bound to IP list
- Authorized MAC list
- Temporary guest list
- IP conflict risk check
➢Alert Conditions: Triggered when devices other than authorized IP and MAC are detected.
➢Real-time Information: Provide real-time status of normal and alert states.
➢Information Collection: Record messages, including the time points of alert issuance and release.
➢Emergency Handling: Immediate notification and execution of predetermined procedures when an alert is triggered.
➢Alert Threshold: Set alert values according to application needs.
Security Measures and Real-time Monitoring
By binding the specified IP and MAC, the system can effectively warn and prevent unauthorized modification behaviors,
allowing information managers to identify and respond to potential security threats in a timely manner.
Practical Operation and Settings
In the actual operation of the WATCHDOG system, the IP/MAC settings can be divided into two parts:
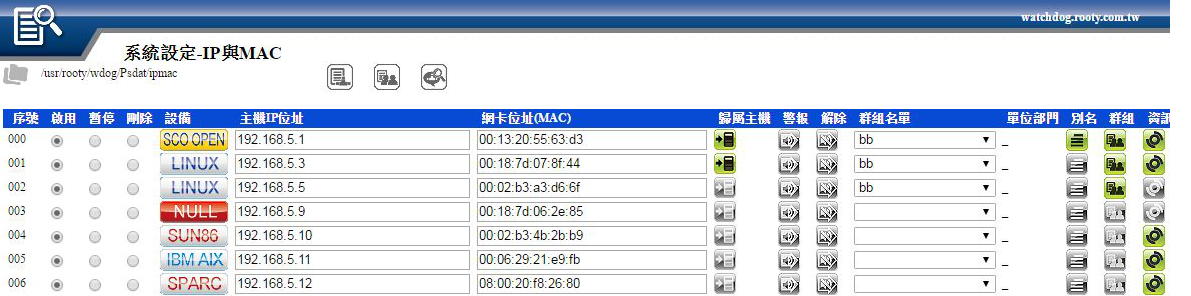
IP and MAC
You can set the specified IP and MAC binding. If the system detects a mismatch, it will issue an alert, and the relevant equipment information of the monitored devices will be displayed.
MAC Control
Here you can adjust more detailed settings for MAC control.
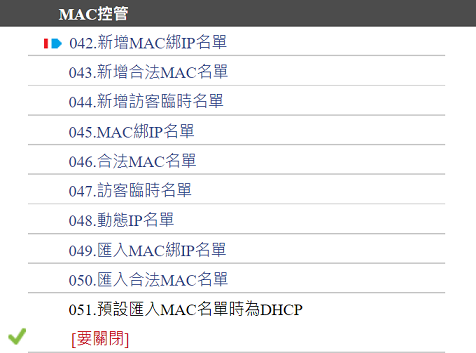
Includes:
➢【Add MAC Bound to IP List】
Define the corresponding relationship between specific MAC addresses and IP addresses to strengthen the identity verification of network devices.
➢【Add Authorized MAC List】
Register recognized MAC addresses as the identification criteria for authorized network devices.
➢【Add Temporary Guest List】
Set up a time-limited MAC address list to control the network access rights of guests or temporary devices.
➢【MAC Bound to IP List】
View the list of MAC and IP bindings.
➢【Authorized MAC List】
View the list of certified MAC addresses as the basis for implementing network policies.
➢【Temporary Guest List】
View the MAC address list of guests or temporary devices to implement time-sensitive access control.
➢【Dynamic IP List】
Operate and maintain a list of dynamically assigned IP addresses, supporting query, modification, and deletion functions.
➢【Import MAC Bound to IP List】
Automatically integrate system-detected MAC and IP information to update the MAC to IP binding list.
➢【Import Authorized MAC List】
Automatically extract authorized MAC addresses from the collected MAC information of the existing system and add them to the list.
➢【Default Import MAC List for DHCP】
Set the default source for automatically importing the authorized MAC list as the DHCP function item. This is a switch setting that can be set to 【On】 or 【Off】.